Harnessing the Power of LOLBins and Macros: A Unique Approach to Executing Executables, by RotPhoenix
Por um escritor misterioso
Descrição

How Do Attackers Use LOLBins In Fileless Attacks? - Phoenix Technology Solutions

Hunting for LoLBins

Threat Hunting: From LOLBins to Your Crown Jewels

Harnessing the Power of LOLBins and Macros: A Unique Approach to Executing Executables, by RotPhoenix

Harnessing the Power of LOLBins and Macros: A Unique Approach to Executing Executables, by RotPhoenix
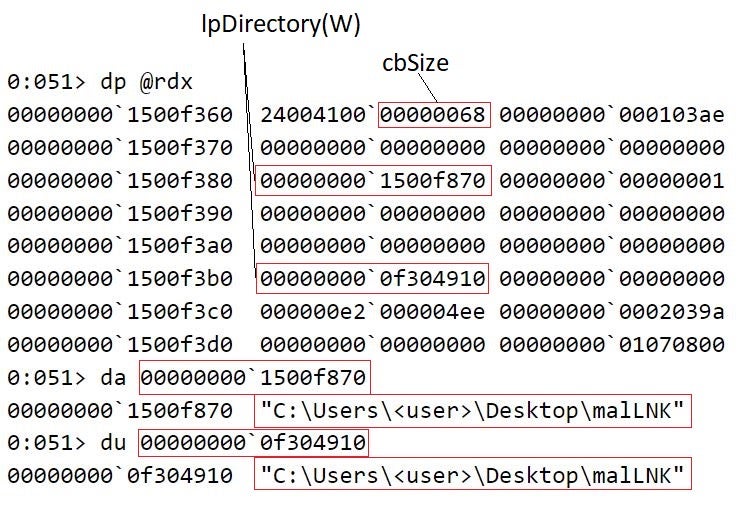
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and Other LOLBins via Windows Shortcuts - SentinelOne
The antecedents of leader-member-exchange (LMX) relationships in African context: the influence of the supervisor's feedback delivery-tactic
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and Other LOLBins via Windows Shortcuts - SentinelOne

Threat Hunting: From LOLBins to Your Crown Jewels

LOLBins: how native tools are used to make threats stealthier

Bring your own LOLBin: Multi-stage, fileless Nodersok campaign delivers rare Node.js-based malware
de
por adulto (o preço varia de acordo com o tamanho do grupo)






