Using an Incident-Focused Model for Information Security Programs
Por um escritor misterioso
Descrição
[nodOrganizations attempt to prevent information security incidents by embedding tools in policies and practices across business functions. Because it is not possible to completely prevent security events, organizations must also include proven response practices as part of their security program. e:summary]

Information & Cyber Security Policy Templates

How to Create an Incident Response Plan (Detailed Guide)

Information Security, Global

What is Incident Management Policy? - Sprinto

How To Conduct A Security Risk Assessment
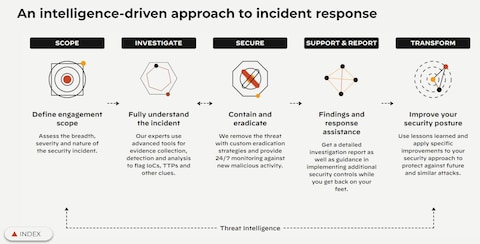
What is Incident Response? - Palo Alto Networks

CIS Critical Security Control 17: Incident Response and Management

NIST Incident Response: Your Go-To Guide to Handling Cybersecurity

A Comprehensive Guide to Managed Detection and Response (MDR

Top 5 Most Common Incident Response Scenarios

The complete information security incident management process

ICS-CERT Incident Response Summary Report - SCADAhacker
de
por adulto (o preço varia de acordo com o tamanho do grupo)





/i.s3.glbimg.com/v1/AUTH_59edd422c0c84a879bd37670ae4f538a/internal_photos/bs/2021/t/L/4AmhOISuSKiDUr5nhhJQ/whatsapp-image-2021-04-25-at-14.38.34.jpeg)

