JUST EXPLOIT - Home
Por um escritor misterioso
Descrição

Zero-Day Exploits & Zero-Day Attacks

Cutter Backyard Bug Control Outdoor Fogger HG-65704, Pack of 6

Navy: Navy/PT-109
Entering the Coin Minefield: Coinminer Malware Campaign Deep-Dive

George Mann on X: Sunday Times: Millionaire philanthropist 'broke trafficking laws to exploit women for sex' #TomorrowsPapersToday / X

Executing a Man-in-the-Middle Attack in just 15 Minutes - Hashed Out

Keep your code safe during the development path using Opensource tools by Filipe Pires
Cyber‐Hygiene Tips During the Time of COVID‐19 IFES - The International Foundation for Electoral Systems

How Our PR Agency Unlocks Brand Potential

Cyber Security Software and Anti-Malware
House Hackers Are Being Accused Online of 'Exploiting' Tenants
VulnHub Sunset Midnight Walkthrough
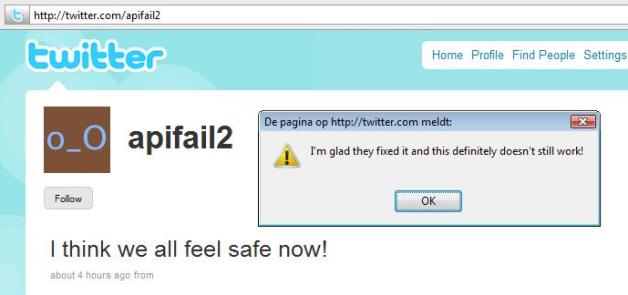
Massive Twitter Security Problem Not Resolved Just Yet
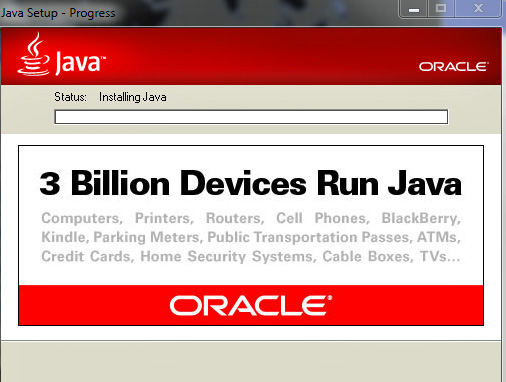
Java users beware: Exploit circulating for just-patched critical flaw

What is the dark web and how do you access it? - Norton
de
por adulto (o preço varia de acordo com o tamanho do grupo)