Inside ImageTragick: The Real Payloads Being Used to Hack Websites
Por um escritor misterioso
Descrição
Get the latest news on how products at Cloudflare are built, technologies used, and join the teams helping to build a better Internet.
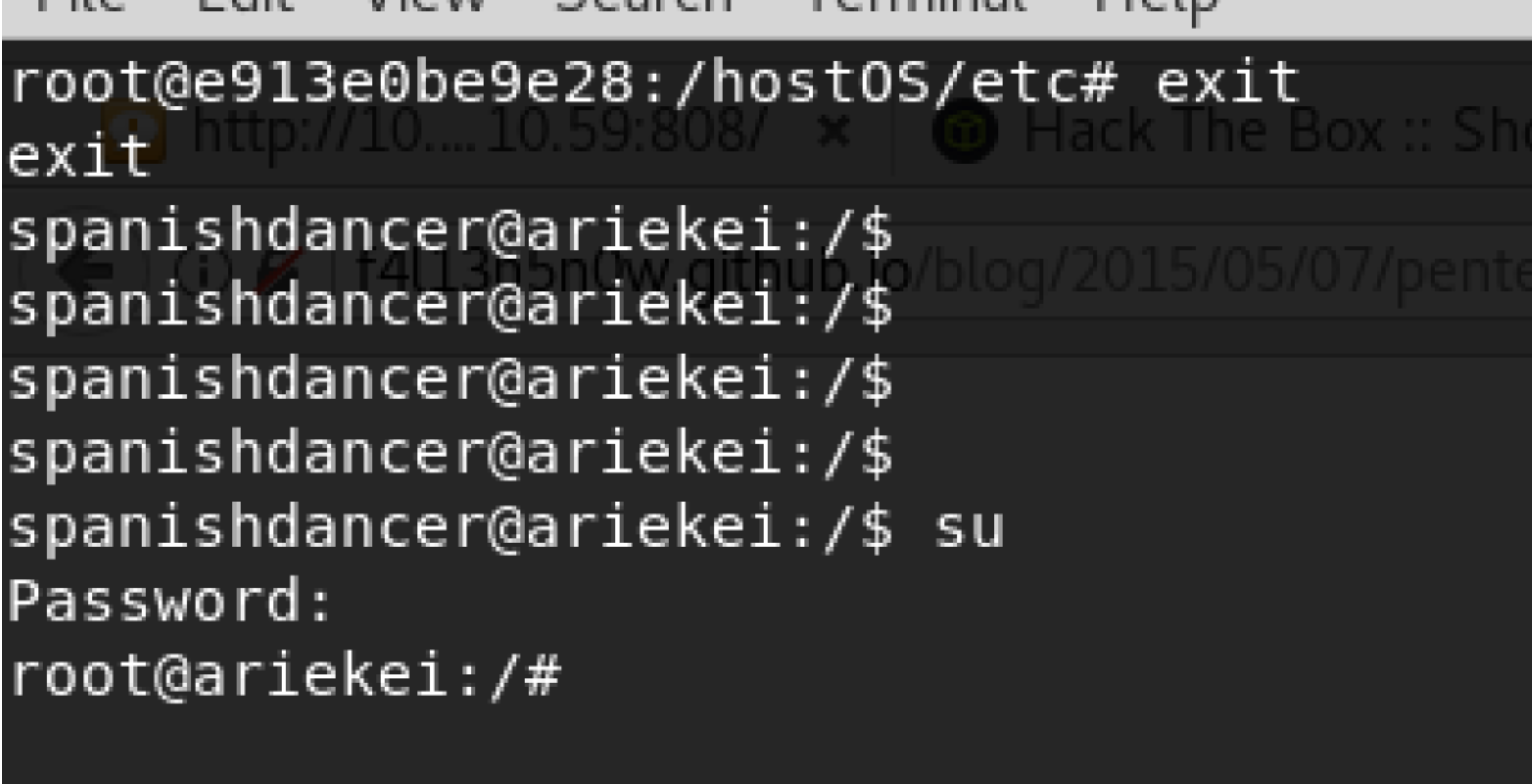
HackTheBox] Ariekei Walkthrough

Agarri : Sécurité informatique offensive

OS Command Injection, Learn AppSec

Bug Bytes #125 - Nuclei for mobile, ImageTragick like it's 2016 & Intro to HTTP/2 and HTTP/3 - Intigriti
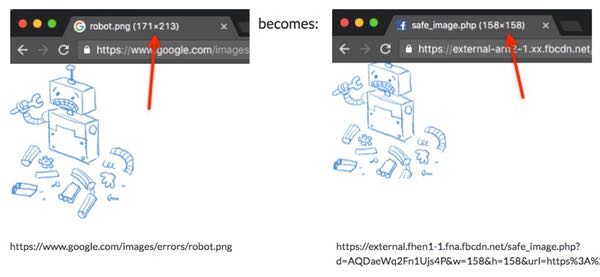
Remote code execution vulnerability affecting Facebook's servers earns researcher $40,000 • Graham Cluley

CanaryStack

How I was hacking docker containers by exploiting ImageMagick vulnerabilities
Wingify CTF 2k21 Wingify Engineering

WAF - The Cloudflare Blog (Page 3)
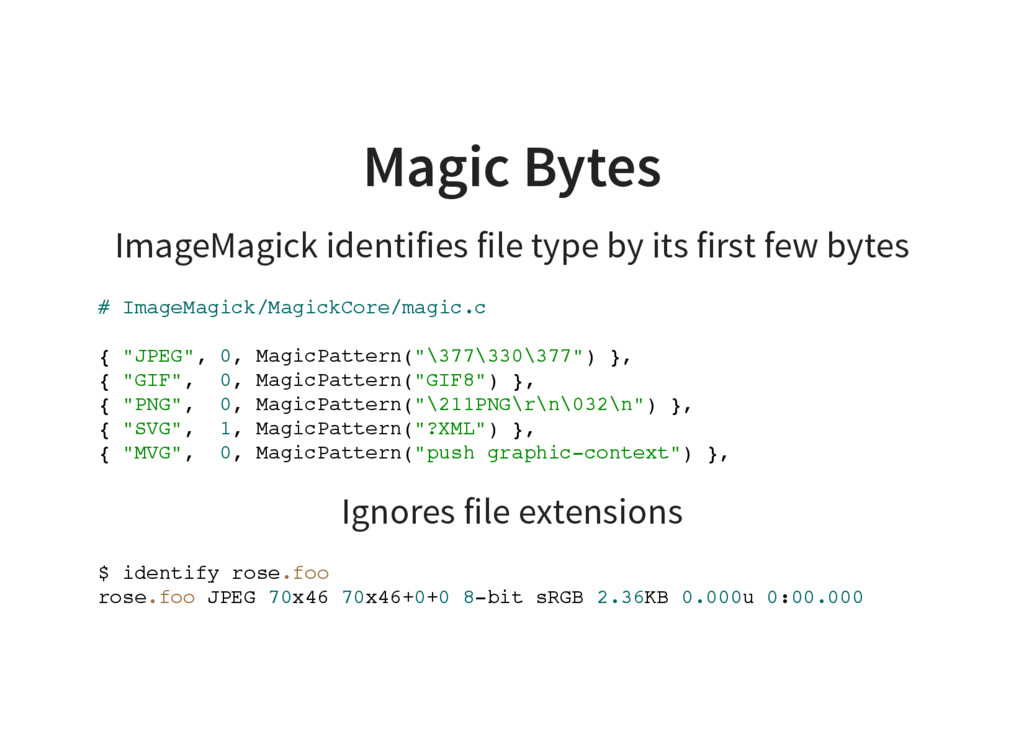
ImageTragick and Rails - Speaker Deck

Ariekei Writeup by Booj - Writeups - Hack The Box :: Forums

How I abused the file upload function to get a high severity vulnerability in Bug Bounty, by Omar Hashem

Cybersecurity: Hacking Windows with Image file Kali Linux

Warning — Widely Popular ImageMagick Tool Vulnerable to Remo - vulnerability database

Ariekei Writeup by Booj - Writeups - Hack The Box :: Forums
de
por adulto (o preço varia de acordo com o tamanho do grupo)







