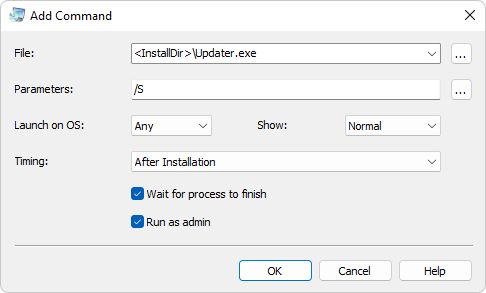
Windows Command Shell — Malware Execution, by Kamran Saifullah
Por um escritor misterioso
Descrição
In my previous article I have talked about Windows Registry Keys i.e. what are they and how attackers/adversaries can alter their values in order to stay persistent and keep on doing what they want…

Windows Command Shell — Malware Execution, by Kamran Saifullah

Search for Prevalence
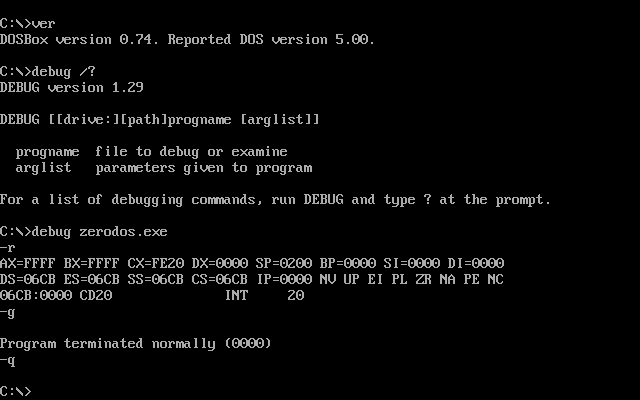
Practical Malware Analysis — Chapter 3 — Lab03–04 — Solution, by Kamran Saifullah

Ahsan Khan posted on LinkedIn

DevTunnels Unleashed

APPENDICES Appendix A1 – Course Syllabi (CISE courses)

DevTunnels Unleashed
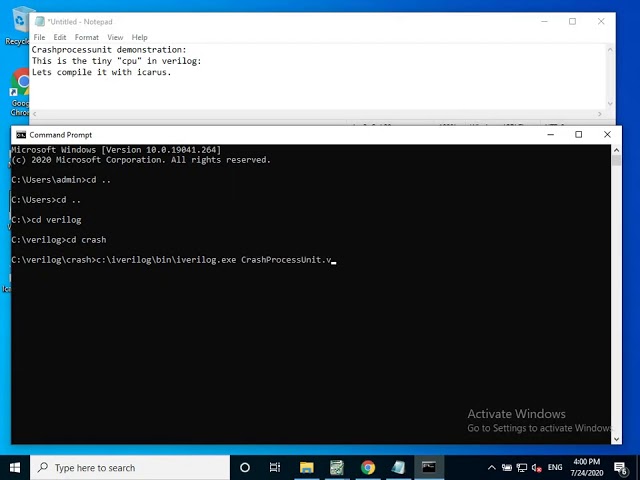
CrashProcessUnit: Stack-based buffer overflow on Icarus Verilog

PDF) Determinants of acute malnutrition among children aged 6–59 months in Public Hospitals, Oromia region, West Ethiopia: a case–control study

PMAT — Bonus Malware Lab Writeup. This article provides my approach to…, by Hacktivities

Epaper_23-03-16 KHI by Pakistan Today - Issuu

Zaid Rehman (OSCP,CIH) على LinkedIn: TryHackMe
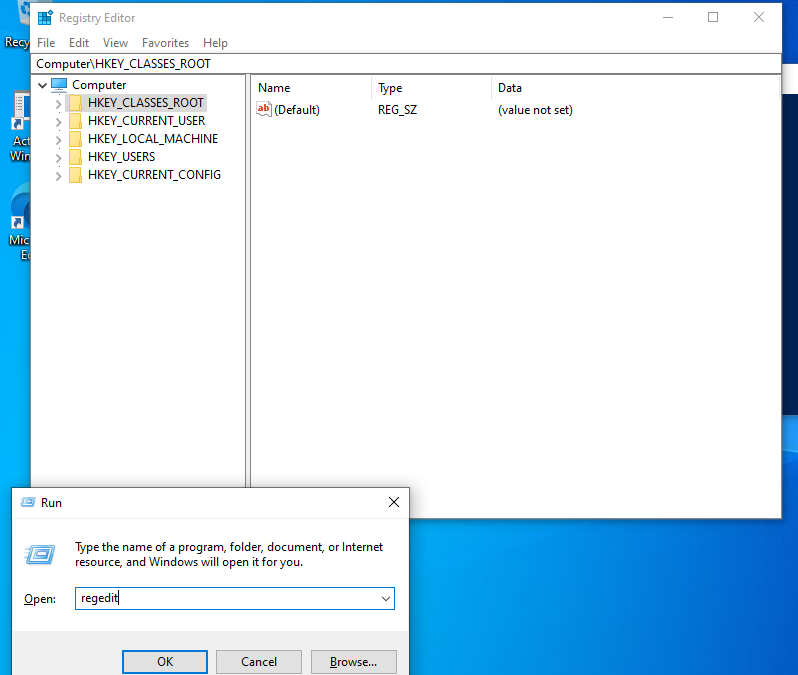
Registry Run Keys / Startup Folder — Malware Persistence, by Kamran Saifullah

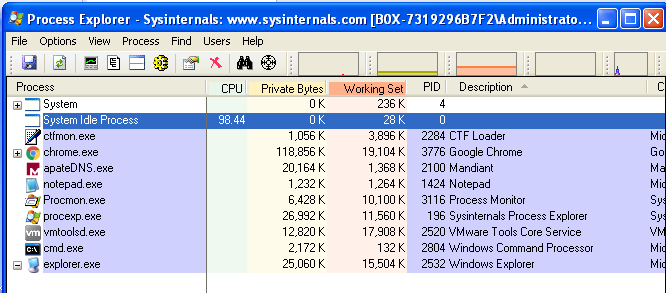
Memory Analysis and Forensics using Volatility - GISPP
de
por adulto (o preço varia de acordo com o tamanho do grupo)
:max_bytes(150000):strip_icc()/psexec-ipconfig-command-5c6ef8dc46e0fb0001b68174.png)